Understanding Phishing Mail McAfee: Safeguarding Your Digital Life
In this digital age, the threat of phishing is omnipresent, with cybercriminals constantly devising new strategies to deceive individuals and organizations. Phishing mail McAfee is a term that signifies the various tactics employed by these malicious actors to trick unsuspecting users into revealing sensitive information. Understanding how phishing works and how McAfee, a leading cybersecurity company, addresses these threats is crucial for anyone who spends time online. The stakes are high; a single phishing attempt can lead to identity theft, financial loss, and significant emotional distress. Thus, it is imperative to equip yourself with knowledge about phishing emails, especially those that could potentially bypass your defenses.
McAfee provides a range of tools and resources to help users identify and counteract phishing attempts effectively. By utilizing advanced algorithms and machine learning, McAfee can detect phishing emails with impressive accuracy. This article aims to explore the various aspects of phishing mail McAfee, including how to recognize such emails, the preventive measures you can take, and how McAfee's software can assist you in staying safe online.
Moreover, we will delve into the common characteristics of phishing emails, understand the consequences of falling victim to these scams, and learn about the best practices for safeguarding personal information. So, let’s embark on this journey to demystify phishing mail McAfee and the threats that lurk in our inboxes.
What is Phishing Mail McAfee?
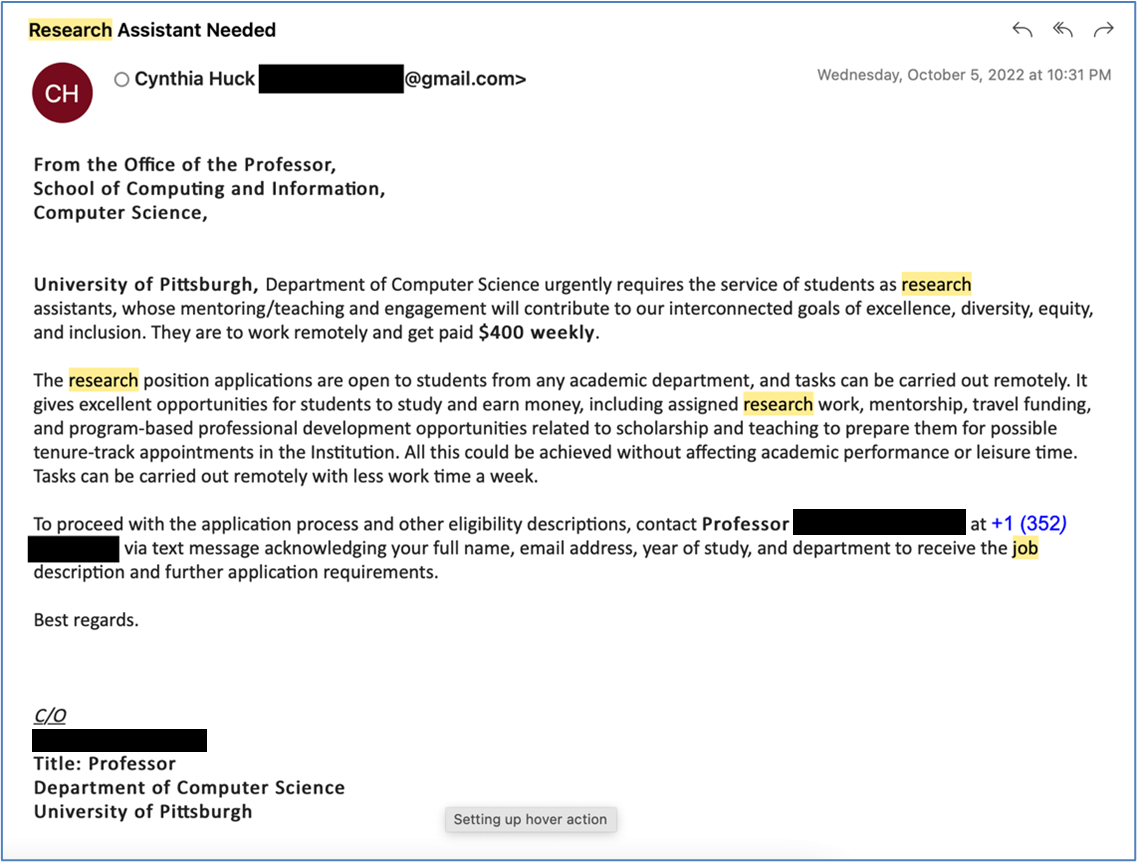
Phishing mail McAfee refers to the deceptive emails that are designed to trick recipients into disclosing personal information such as passwords, credit card numbers, or bank account details. These messages often appear to come from reputable sources, including banks, social media platforms, or even McAfee itself. They typically contain links to fake websites that resemble legitimate ones, further adding to their credibility.
How Does Phishing Work?
Phishing operates on the principle of manipulation. Cybercriminals exploit human emotions, such as fear, urgency, or curiosity, to prompt users to take immediate action. Here’s how phishing typically unfolds:
- The victim receives an email that appears legitimate.
- The email contains a call to action, such as "Verify your account" or "Update your payment information."
- The recipient is directed to a fraudulent website that looks like the real one.
- Once on the site, they are prompted to enter sensitive information.
What Are the Red Flags of Phishing Emails?
Identifying phishing emails is crucial for protecting yourself. Here are some common red flags to look out for:
- Unusual sender email addresses.
- Generic greetings, such as "Dear Customer."
- Spelling and grammatical errors.
- Urgent language that pressures you to act quickly.
- Links that do not match the supposed sender's domain.
How Can McAfee Help Combat Phishing?
McAfee offers several tools and features designed to combat phishing attacks:
- Email Protection: Scans emails for known phishing threats.
- Web Protection: Alerts users when attempting to visit suspicious websites.
- Identity Theft Protection: Monitors personal information for unauthorized use.
- Real-Time Threat Updates: Provides users with the latest information on emerging phishing threats.
What Should You Do If You Receive a Phishing Email?
If you suspect that you've received a phishing email, take the following steps:
- Do not click on any links or download attachments.
- Verify the sender's email address.
- Contact the organization directly using official contact information.
- Report the phishing attempt to your email provider.
- Consider using McAfee's tools to scan your device for threats.
How Can You Protect Yourself from Phishing Attacks?
Protecting yourself from phishing attacks involves a combination of awareness and technology:
- Educate yourself about the signs of phishing.
- Use strong, unique passwords and enable two-factor authentication wherever possible.
- Regularly update your software and security solutions like McAfee.
- Be cautious when sharing personal information online.
What Are the Consequences of Falling for Phishing Emails?
The repercussions of falling victim to phishing emails can be severe:
- Identity theft, leading to financial loss and damaged credit.
- Loss of personal data, including photos and documents.
- Unauthorized transactions or fraudulent charges.
- Emotional distress and a sense of violation.
Can McAfee Help Recover from a Phishing Attack?
While McAfee cannot reverse the damage caused by a phishing attack, it can provide valuable tools for recovery:
- Identity Theft Recovery Assistance: Helps victims navigate the recovery process.
- Monitoring Services: Alerts you if your personal information appears on the dark web.
- Data Encryption: Protects sensitive files, reducing the risk of future breaches.
How Can You Stay Informed About Phishing Threats?
Staying informed about the latest phishing threats is essential for maintaining your security:
- Subscribe to cybersecurity newsletters.
- Follow cybersecurity blogs and forums.
- Utilize resources provided by McAfee and other security companies.
In conclusion, phishing mail McAfee represents a significant threat to individuals and organizations alike. By understanding the nature of phishing, recognizing its signs, and utilizing tools like McAfee, you can safeguard your digital life. Stay vigilant, informed, and proactive in your cybersecurity efforts to minimize the risks associated with phishing attacks.
Article Recommendations
- Cancer Weekly Horoscope
- Sophierain Nudes
- Catherine Bell Partner
- Jackerman
- Is Barron Trump Gay
- Jessica Springsteen Married
- Bloxburg Job Salary List 2024
- Kelly Monaco
- Dr Yang Greys Anatomy
- Nayib Bukele Religion